Merkle proofs, full chain validation, and third-party verifiable integrity for every record in the Provenance Vault. Prove any entry is untampered without exposing the rest of the chain.
Cryptographic proof of every AI governance decision.
Verify any individual entry's integrity by recomputing its SHA-256 hash against the stored value.
Walk the entire chain from any entry back to genesis, verifying every link in the sequence.
Generate compact cryptographic proofs that any entry exists in the chain without revealing other entries.
Xybern provides cryptographic verification tools for proving the integrity of any record in the Provenance Vault.
Choose any verification record from the Provenance Vault to validate its integrity and chain position.
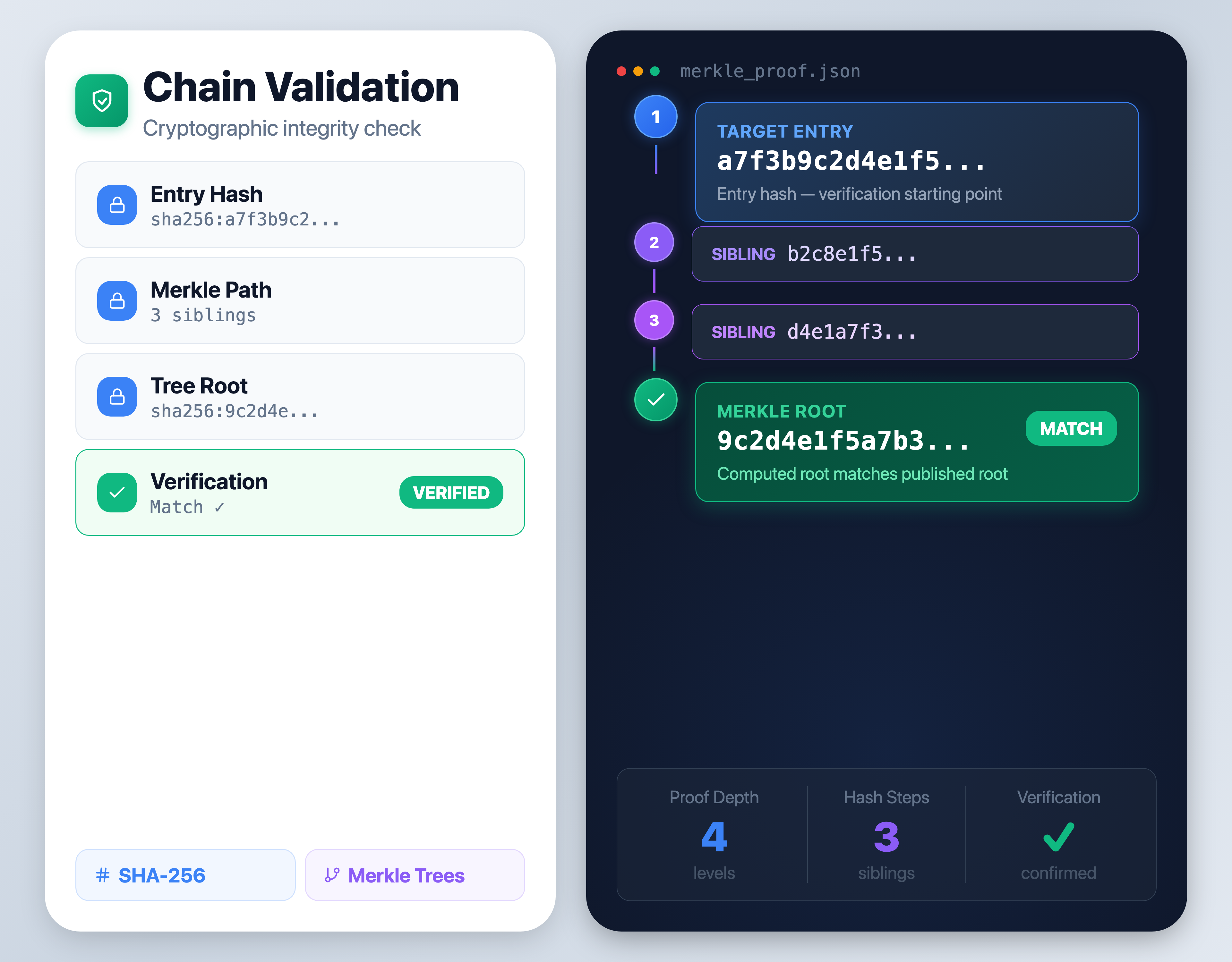
Cryptographic proof is computed from the entry hash through the Merkle tree to the root, creating a verifiable path.
Proof is verified against the published root hash, confirming the record is untampered and authentic.
SHA-256 hash of selected verification record
Sibling hashes along proof path through the tree
Computed root hash from proof path recombination
Computed root matches published root — integrity confirmed
The cryptographic proof format used for third-party verification of any entry in the chain.
{
"entry_id": "ent_1847",
"entry_hash": "sha256:a7f3b9c2d4e1f5...",
"proof": {
"leaf": "sha256:a7f3b9c2d4e1f5...",
"path": [
{"hash": "sha256:b2c8e1f5...", "position": "right"},
{"hash": "sha256:d4e1a7f3...", "position": "left"},
{"hash": "sha256:f7a3c2b8...", "position": "right"}
],
"root": "sha256:9c2d4e1f5a7b3..."
},
"verified": true,
"verified_at": "2025-01-15T14:35:00Z"
}Three independent methods to verify the integrity of any record in the Provenance Vault.
Recompute the SHA-256 hash of any entry and compare against the stored value for instant integrity verification.
Traverse the chain from any entry back through every predecessor, verifying hash links at each step.
Generate a compact cryptographic proof path from any entry to the Merkle root for third-party verification.
Retrieve Merkle proofs programmatically for any entry in the Provenance Vault.
Returns the full Merkle proof path for the specified entry, including proof type, sibling hashes, root hash, and verification status.
The response includes the verified boolean and the chain depth, enabling immediate integrity confirmation.
GET /api/sentinel/vault/v2/entries/ent_1847/proof
// Response
{
"entry_id": "ent_1847",
"proof_type": "merkle",
"proof_path": ["sha256:b2c8...", "sha256:d4e1...", "sha256:f7a3..."],
"root_hash": "sha256:9c2d4e1f...",
"verified": true,
"chain_depth": 1847
}Cryptographic proof of integrity for every AI governance record in the Provenance Vault.